
Overview
The Certified Ethical Hacker (CEH) credential is the most trusted ethical hacking certification and accomplishment recommended by employers globally. It is the most desired information security certification and represents one of the fastest-growing cyber credentials required by critical infrastructure and essential service providers.
Since the introduction of CEH in 2003, it is recognized as a standard within the information security community. CEH v11 continues to introduce the latest hacking techniques and the most advanced hacking tools and exploits used by hackers and information security professionals today. The Five Phases of Ethical Hacking and the original core mission of CEH remain valid and relevant today: “To beat a hacker, you need to think like a hacker.”
Tools Covered







- Degree Levels: Bachelors,Masters
- Field of Studies: Information Technology
- Prior Job Experience: NA
- Other Programs:
- Business/Marketing Heads & Executives
- C-Suite Employees responsible for determining and achieving Revenue Targets
- Sales Heads & Executives
- IT employees assigned for assisting Sales, Marketing and Business Analytics Departments
- Students/graduates with business, commerce, marketing background
- Exam 77-420:Microsft Excel 2013
- SQL Relational Databases 101
Course Outline
- Week 1
- Week 2
- Introduction to Course
- Networking for Hackers
- Linux for Hackers (Administration)
- Introduction to Ethical Hacking
- Understanding the Elements of Information Security
- Understanding Information Security Attacks & Warfare
- Overview of Cyber Kill Chain Methodology, TTPs, and IoCs
- Overview of Hacking Concepts, Types & Phases
- Understanding Ethical Hacking Concepts and its scope
- Overview of Information Security Controls Overview of Pakistan Cybersecurity Law's
- Linux Administration
- Installing Linux
- Understanding Network Scanning Concepts
- Understanding various Scanning Tools
- Understanding Various Host Discovery and Port Scanning Techniques
- Understanding OS Discovery
- Understanding various Techniques to Scan Beyond IDS and Firewall
- Drawing Network Diagrams
- Understanding Footprinting Concepts
- Understanding Footprinting through Search Engines and Advanced Google Hacking Techniques
- Understanding Footprinting through Web Services and Social Networking Sites
- Understanding Website Footprinting and Email Footprinting
- Understanding WHOIS, DNS and Network Footprinting
- Understanding Footprinting through Social Engineering
- Understanding different Footprinting tools and Countermeasures
- Week 3
- Week 4
- Overview of Vulnerability Research, Vulnerability Assessment and Vulnerability Scoring System
- Overview of Vulnerability Management Life Cycle ( Vulnerability Assessment Phases)
- Understanding various types of Vulnerabilities and Vulnerability Assessment Techniques
- Understanding Different Approaches of Vulnerability Assessment Solutions
- Understanding various types of Vulnerabilities Assessment Tools and Criteria for Choosing Them
- Vulnerability Assessment Tools
- Generating and Analyzing Vulnerability Assessment Reports
- Understanding Enumeration Concepts
- understanding Different Techniques for NetBIOS Enumeration
- Understanding Different Techniques for SNMP and LDAP Enumeration
- Understanding Different Techniques for NTP and NFS Enumeration
- Understanding Different Techniques for SMTP and DNS Enumeration
- Understanding Other Enumerations such as IPsec, VoIP, RPC, Linux/Unix, Telnet, FTP, TFTP, SMB, IPv6 and BGP Enumeration
- Understanding Different Enumeration Countermeasures
- Understanding Malware and Malware propagation Techniques
- Understanding Advanced Persistent Threats(APTs) and their Lifecycle
- Overview of Trojans, their Types and how they infect Systems
- Overview of Viruses, their Types and how they infect Systems
- Overview of Computer Worms and Fileless Malware
- Understanding the Malware Analysis Process
- Understanding Different Techniques to Detect Malware
- Understanding different Malware Countermeasures
- Overview of CEH Hacking Methodology
- Understanding Techniques to Gain Access to the System
- Understanding Privilege Escalation Techniques
- Understanding Techniques to create and Maintain Remote Access to the System
- Overview of Different types of Rootkits
- Overview of Steganography and Steganalysis Techniques
- Understanding Techniques to hide the evidence of compromise
- Understanding Different System Hacking Countermeasures
- Week 5
- Week 6
- Understanding Social Engineering Concepts
- Understanding Various Social Engineering Techniques
- Understanding Insiders Threats
- Understanding Impersonation on Social Networking Sites
- Understanding Identity Theft
- Understanding Different Social Engineering Countermeasures
- Understanding Different DOS/DDos Attack Tools
- Understanding Different Insiders threats and Identity Theft Countermeasures
- Overview of Denial-of-Service(DOS) and Distributed Denial-of-service(DDoS) Attacks
- Understanding Different DoS/DDoS Countermeasures
- Overview of Sniffing Concepts and Techniques
- Overview of Various Sniffing Tools
- Understanding different Sniffing Countermeasures
- Understanding Web Application Concepts
- Understanding Web Application Threats
- Understanding Web Application Hacking Methodology
- Overview of Web Application Hacking Tools
- Overview of Web APIs, Webhooks and Web Shell Concepts
- Overview of Web Application Security Testing Tools
- Understanding SQL Injection With its types of Attacks
- Understanding of SQL Injection Methodologies
- Understanding of Web Server Concepts and its Attacks
- Understanding Web Server Attack Methodology And Attack Tools
- Understanding Patch Management Concepts
- Overview of Web sever Security Tools
- Understanding Different Wen Server Attack Countermeasures
- Week 7
- Week 8
- Understanding Mobile Platform Attack Vectors
- Understanding Hacking Android OS
- Understanding Cryptography Concepts
- Overview of Encryption Algorithms and Cryptography tools
- Understanding Email and Disk Encryption
- Understanding Cryptography Attacks along with Cryptoanalysis Tools
- Overview Of Wireless Concepts and Encryption Algorithms
- Understanding Wireless Hacking And Wireless Hacking Methodology
- Understanding Bluetooth Hacking Techniques
- Overview of Wireless Hacking Countermeasures and Security Tools
- CTF (VulnHub, TryHackMe, HackTheBox)
- Bug Bounty
- Security Operation Center (SOC)
- SIEM Solutions Overview (Wazuh, Splunk, IMB Qradar)
- Final Project
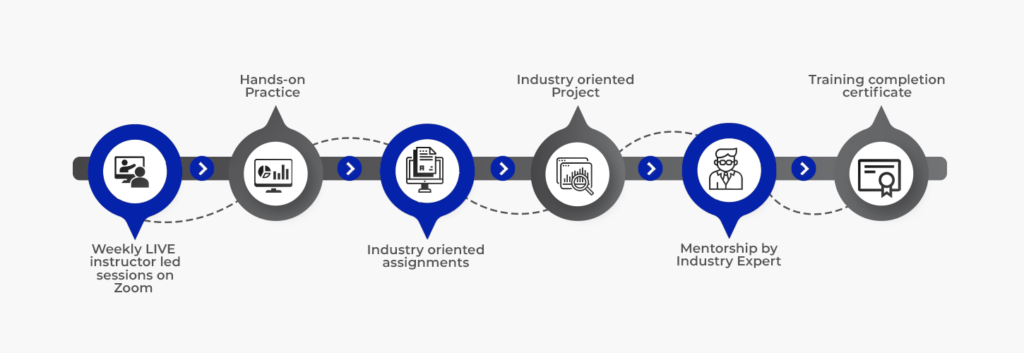
Our Methodology
Industry Usecases
With real world projects and immersive content built in partnership with top tier companies, you’ll master the tech skills companies want.
Technical Support
Our knowledgeable mentors guide your learning and are focused on answering your questions, motivating you and keeping you on track.
Career Mentorship
You’ll have access to resume support, portfolio review and optimization to help you advance your career and land a high-paying role.
Frequently Asked Questions
Yes, You will be awarded a course completion certificate by Dice Analytics if you pass the course.
Since our trainings are led by Industry Experts so it is made sure that content covered in workshop is designed with hand on knowledge of more than 70-75 % along with supporting theory.
For this professional workshop, you need to have a PC with minimum 4GB RAM and ideally 8GB RAM.
Don’t worry! We have got you covered. You shall be shared recorded lectures after each session, in case you want to revise your concepts or miss the lecture due to some personal or professional commitments.
Yes, you can rejoin the training within the span of an year of your registration. Please note following conditions in case you’re rejoining.
1) There are only 5 seats specified for rejoiners in each iteration.
2) These seats will be served on first come first basis.
3) If you have not submitted your complete fee, you may not be able to rejoin. Your registration would be canceled


